What is the ASD Essential Eight?
The ASD developed the Essential Eight to help organisations protect their networks, systems, and data from cyber threats. It covers a basic set of security practices organisations should implement to protect their assets from malicious actors.
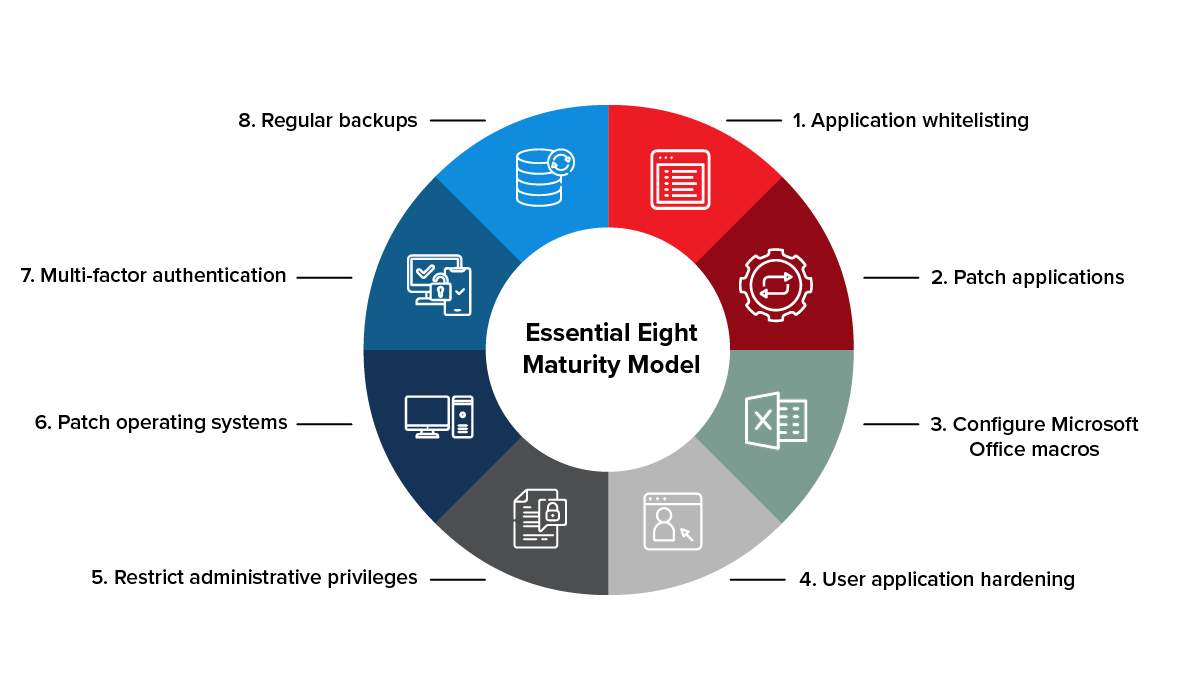
The Essential Eight strategies cover key areas of concern for many organisations. These include:
- Application control
- Patch applications
- Configure Microsoft Office macro settings
- User application hardening
- Restrict administrative privileges
- Patch operating systems
- Multi-factor authentication
- Regular backups
These strategies minimise the risk of a successful cyber-attack by reducing the attack surface and preventing malicious actors from accessing an organisation’s systems. The strategies are ranked according to maturity level – meaning the risks an organisation faces related to increasing levels of threat actor tradecraft.
- Level 0: Shows weaknesses in an organisation’s overall cyber security posture.
- Level 1: An organisation can likely hold its own against a non-committal attack that uses basic tradecraft and tools.
- Level 2: The organisation is ready to handle attacks from a more committed attacker.
- Level 3: Indicates the organisation can mitigate attacks from a dedicated threat actor using advanced tradecraft and techniques.
Benefits of the Essential Eight
- Clear and simple: Provides clear, measurable, black-and-white steps for organisations that want to lower their risk of data breaches.
- Addresses technical vulnerabilities: The strategies in the Essential Eight focus on technical vulnerability mitigation.
- Easy to check your organisation for compliance: With such clear, black-and-white outcomes, it’s easier for an organisation to show how well they comply with a certain level of maturity.
- Easy to choose a maturity level based on risk: The range of maturity levels allows an organisation to mitigate a level of tradecraft they are likely to face, aligning the Essential Eight to their risk management goals.
Challenges of the Essential Eight
- Requires advanced technical knowledge: The content of the strategies can be challenging for non-technical staff to understand, implement, or appreciate.
- Narrow focus: The Essential Eight does not account for business activities and behavioural elements that might contribute towards these risks.
- Can be intrusive: While some elements of the Essential Eight are relatively simple to accomplish, others can take significant resources and interrupt daily operations.
Who is the Essential Eight for?
Given that the Australian government has developed the Essential Eight, it’s little wonder that it is mandatory for other government agencies. It’s also no surprise that businesses and organisations that work alongside these agencies – either directly or as part of the supply chain – will be interested in reaching a level of compliance that makes them attractive to these agencies.
However, not just the government ecosystem benefits from the Essential Eight. If your company prefers a checklist approach to cyber security – and has the in-house or outsourced capability to make it happen – you can use the Essential Eight to identify gaps in your cyber security posture and make changes that suit the organisation’s level of risk.
What is the NIST Cybersecurity Framework?
The NIST Cybersecurity Framework (CSF) is a voluntary, risk-based approach to managing cyber security risk. Developed by the National Institute of Standards and Technology (NIST), the CSF provides a common language and structure for organisations to identify, assess, manage, and communicate their cyber security risk.
The framework helps organisations of all sizes identify, prioritise, and manage risks per their organisational goals. It consists of five core functions:
- Identify
- Protect
- Detect
- Respond
- Recover
The core functions include categories and subcategories outlining comprehensive activities for managing risk. The framework also features guidance on measuring an organisation’s cyber security risk and provides a common language for a company to communicate risk to its stakeholders.
The functions include:
- Risk management process: Relates to functionality and repeatability of cyber security risk management.
- Integrated risk management program: Measures how cyber security influences risk management decisions.
- External participation: Tracks the degree to which the organisation monitors and manages supply chain risk and shares information with outside parties.
The idea is to develop desired outcomes based on core factors that define the entire breadth of cyber security. The cores span prevention and recovery actions, translating these elements into actionable language that an organisation’s stakeholders understand.
NIST CSF encourages organisations to consider business requirements and material risks and use these measures to make reasonable and informed cyber security decisions. The framework then helps identify and address feasible and cost-effective improvements.
The CSF enables flexibility and allows organisations to tailor their approach to managing cyber security risk based on their unique risk profile and organisational goals.
Benefits of the NIST CSF
- Flexible, adaptable framework: The CSF’s outcome-driven approach makes it highly flexible across various industries and company sizes, with future-facing actions that let organisations update their strategies in response to changing demands.
- Enable long-term view of cyber security: The CSF helps remove the ‘one-off’ audit compliance mindset, replacing it with a more adaptive and responsive posture.
- Maps to other frameworks: The behavioural elements of the NIST CSF can easily be mapped to other cyber security controls, which means that organisations can meet their compliance requirements while strengthening their overall cyber security stance.
- Widely recognised: NIST CSF represents the collective experience of thousands of information security professionals. It forms the basis of industry best practices by being any framework’s most comprehensive, in-depth set of controls.
- Connect technical and business side stakeholders: The CSF’s risk-based approach makes it compatible with the priorities of organisational executives. This approach helps align the integrated risk management approach necessary for cyber security management to broader business goals, enabling better communication and decision-making through a shared security vocabulary.
Challenges of the NIST CSF
- Relies on understanding existing standards: The NIST CSF is non-prescriptive, meaning it does not deliver a detailed checklist to follow. Instead, organisations are encouraged to follow standards that meet their risk management needs. If an organisation is unfamiliar with the standards referenced in the framework, it may struggle to implement the required actions.
- Technical communication is a must: The NIST CSF requires a thorough understanding of an organisation’s current cyber security risk profile to drive the organisation’s adoption and execution of a remediation plan. While this can encourage buy-in from key stakeholders, it also requires a level of technical communication that may be outside the capacity of some organisations.

What are the key differences between the NIST Cybersecurity Framework (CSF) and ASD Essential Eight?
- The NIST CSF is voluntary and provides organisations with a risk-based approach to cyber security. The ASD Essential Eight outlines mandatory cyber security controls that all Australian government entities must implement.
- The NIST CSF provides organisations with comprehensive best practices and guidelines for managing their cyber security risk. The ASD Essential Eight outlines specific, mandatory controls to reduce the risk of cyber-attacks.
- The NIST CSF use five core functions: identify, protect, detect, respond, and recover. The ASD Essential Eight specifies eight controls: application control, patch applications, configure Microsoft Office macro settings, user application hardening, restrict administrative privileges, patch operating systems, multi-factor authentication and regular backups.
- The NIST CSF provides organisations with a risk-based approach to cyber security, while the ASD Essential Eight is a prescriptive set of controls.
Which one is right for my organisation?
Ultimately, the choice between NIST CSF and the Essential Eight depends on various factors specific to your organisation, including regulatory requirements, resource availability, risk profile, and industry standards.
Here is a breakdown of the key points to consider:
- Regulatory compliance: Your industry or location might subject you to regulatory requirements. NIST is widely recognised and used in various sectors, especially in the United States. Ensure that your chosen framework aligns with the regulatory standards applicable to your organisation.
- Scope and focus: NIST provides comprehensive cyber security guidelines that cover various aspects of cyber security, including risk management, incident response, and security controls. On the other hand, the Essential Eight focuses specifically on eight controls for mitigating the risk of cyber security incidents. Consider the scope and focus of each framework and determine which one better suits your organisation’s needs and priorities.
- Level of detail: NIST is detailed and extensive, offering in-depth recommendations and best practices for cyber security. In contrast, the Essential Eight provides a more concise set of controls. Consider the level of detail required for your organisation’s cyber security efforts and choose the framework that provides the appropriate level of guidance.
- Resource availability: Implementing cyber security frameworks requires resources, including time, budget, and expertise. Consider the availability of resources within your organisation for implementing and maintaining the chosen framework. Some organisations may find it more feasible to implement the Essential Eight due to its focused approach, while others may have the resources to adopt and maintain NIST.
- Risk profile: Assess your organisation’s risk profile and cyber security maturity level. NIST provides a risk-based approach to cyber security, allowing organisations to tailor efforts based on their specific risk profile. Evaluate whether your organisation requires the comprehensive risk management approach offered by NIST or if the recommended Essential Eight controls adequately address your concerns.
- Industry best practices: Consider industry best practices and standards relevant to your organisation. NIST is widely adopted across various industries and considered a benchmark for cyber security best practices. However, the Essential Eight has gained recognition, particularly in Australia and other regions where the ASD’s guidance carries influence. Evaluate which framework aligns better with industry best practices relevant to your organisation.
- Flexibility and adaptability: Choose a flexible and adaptable framework to accommodate technological advancements and changes in the threat landscape. The NIST and the Essential Eight frameworks emphasise adaptability and continuous improvement in cyber security practices.
Finally, your organisation may find it beneficial to consult with a trusted IT advisor or cyber security partner, as they may have insights about your IT environment, which also come into play.

Conclusion
Australian SMEs face a complex landscape of cyber threats. Choosing the right compliance framework – the Essential Eight or NIST CSF – can significantly improve your security posture. But navigating the differences and selecting the optimal approach can be overwhelming.
Netier can help you apply the right compliance framework
We’re experts in IT and cyber security management, dedicated to empowering Australian SMEs. Here’s how we can assist:
- Compliance Framework Selection: We’ll analyse your unique needs, regulations, and risk profile to recommend the best fit – Essential Eight’s clear controls or NIST CSF’s comprehensive approach.
- Implementation and Management: Our team will guide you through implementing the chosen framework, ensuring seamless integration with your existing systems.
- Ongoing Support: We offer continuous monitoring, maintenance, and expert advice to keep your security measures robust and adaptable.
Stop wondering which framework is right. Let Netier be your trusted partner in building a secure and resilient IT environment. Contact us today for a free consultation!




