1. Understand the most pertinent threats to your business
While the news often covers ransomware attacks on large enterprises, small organisations are just as at risk. Due to the financial and operational repercussions, an attack like this can inflict damage that the organisation will struggle to recover from. Phishing attacks and social engineering are often the gateways to threat actors deploying ransomware.
Sensitive data such as login credentials or financial information might also impact your company. Between January and June of 2023, the Office of the Australian Information Commissioner (OAIC) received 409 notifications of data breaches, with cyber incidents like ransomware and phishing accounting for 42% of these breaches.
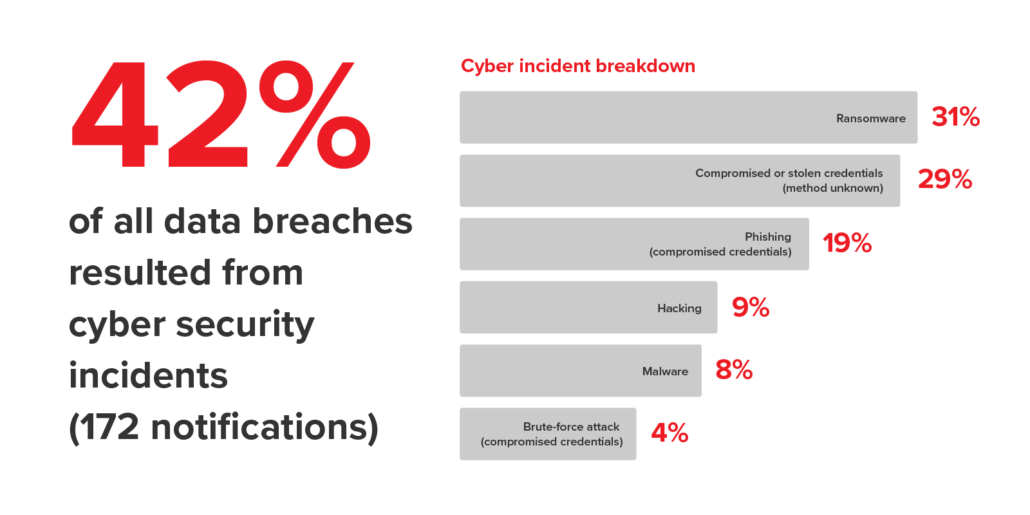
Source: OAIC.
2. Implement and revisit cyber security controls
Implement essential cyber security controls available to you, such as enforcing multi-factor authentication (MFA), regularly updating applications and operating systems to limit vulnerabilities, and using password managers. A Technology Success Partner can also guide your cyber security strategy by implementing and managing solutions such as email filtering, managed detection and response, and endpoint management.
Applying these measures is just the start. Cyber security requires ongoing review and adaptation. Threats evolve daily, so we need to evolve and adapt to counter them. What worked ten years ago is unlikely to work today. Many threat actors take advantage of ‘set and forget’ security for this very reason.

3. Train staff on cyber security habits and response procedures
Your staff have a role to play in maintaining cyber security. Regardless of their position, every employee can be a point of strength or vulnerability in your cyber defence. Training people on cyber security best practices when they join your organisation and running refresher courses is a proactive way to improve your security posture.
Recognising phishing attempts should be a key point of training. Your team can prevent potential breaches by recognising signs of phishing, such as suspicious links and urgent requests for information. Additionally, educating people on best practices for protecting their accounts can go a long way in preventing unauthorised access.
Regular training also prepares people to respond appropriately to potential cyber threats. Keeping everyone up-to-date on the latest cyber security practices and threat scenarios equips them with the knowledge to act decisively. Response procedures should be clear and practised regularly so staff know exactly what steps to take during a cyber incident, reducing the potential impact on the business.

4. Align with necessary compliance requirements
Aligning with compliance frameworks is an excellent way to improve your company’s cyber security posture proactively. Frameworks like the Essential Eight, developed by the Australian Cyber Security Centre (ACSC), offer structured approaches to improving cyber resilience. These frameworks outline key strategies and controls that can significantly mitigate the risk of cyber attacks when effectively implemented.
However, it’s critical to understand that compliance with frameworks such as the Essential Eight is not a silver bullet. These frameworks provide a solid foundation of controls designed to enhance cyber security but are not infallible against all cyber threats. Your organisation should view them as part of a broader cyber security strategy, including ongoing risk assessments, staff training, and adopting additional security measures tailored to specific threats.
Identifying the right compliance framework for your organisation is also essential. Not all frameworks will be relevant or necessary for every business. Factors such as the nature of your operations, the sensitivity of the data you handle, and specific industry regulations should guide your compliance strategy.
5. Develop an incident response and recovery plan
Preparing for a cyber attack can minimise an incident’s impact and ensure the organisation responds in a quick and structured manner, reducing downtime and financial loss.
An incident response and recovery plan should establish:
- Clear communication channels: Define who will receive notifications of the breach.
- Roles and responsibilities: Specify tasks for team members to ensure an organised and efficient response.
- Specific response procedures: Outline steps tailored to different cyber incidents, detailing how to contain, eradicate, and recover from each.
- Notification procedures: Identify when and how to notify external parties, including regulatory bodies or impacted customers.
- Recovery and return to normal operations: Provide a step-by-step process for restoring affected systems and resuming business activities.
- Post-incident review processes: Implement a mechanism for analysing the incident to learn and improve future cyber defences.
Regularly testing and updating your incident response and recovery plan is essential. By continually refining the plan based on these exercises and any real incidents, organisations can stay ahead of potential threats and ensure resilience against cyber attacks.
Conclusion
Regardless of your company’s size, proactive cyber security strategies are essential to preventing attacks and their impacts. You must understand threats, implement security controls, train staff, adhere to compliance, and craft an incident response plan.
Cyber security demands constant vigilance and consistent updates. By staying informed, fostering awareness, and revisiting security practices, your business can maintain a strong defence against evolving threats. Partnering with cyber security experts who can provide additional support and insights ensures your business remains resilient now and in future.
Netier can guide your proactive cyber security strategy
At Netier, we stand by the principle that proactivity is the best defence in cyber security. If your strategy needs refining or you’re seeking ways to bolster your cyber security measures, we’re here to help. Our security experts will review your current systems and develop a strategy to protect your business and enhance its resilience. Visit our Security page for more information on how we can support you.



